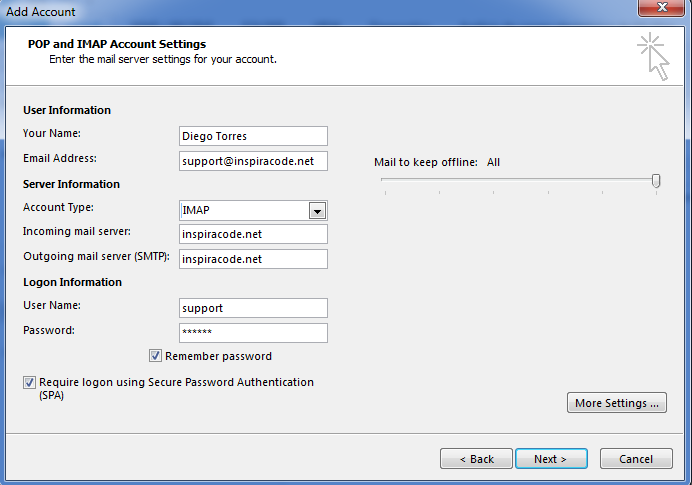
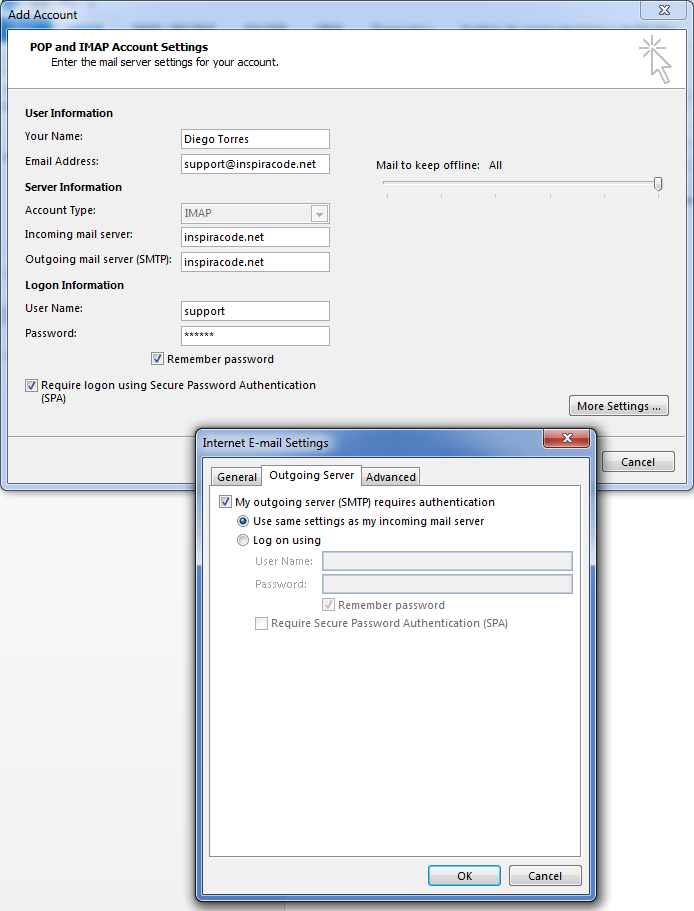
In previous posts, setting up an Email Server, we Listed the required assets and Uploaded the SSL certificates to the server
In this post we will install and configure Postfix and Dovecot to inbound and outbound email using IMAP protocol.
First thing is to remove sendmail from our server (the default MTA installed in our Fedora distribution):
$ sudo yum remove sendmail
Then we install postgres:
$ sudo yum install postgres
Once installed, we will configure to resolve to our domain and listen to our email ports:
$ sudo vi /etc/postfix/main.cf
Set the following values in the postfix main.cf:
$ sudo vi /etc/postfix/main.cf
# line 75:
myhostname = inspiracode.net # (your domain name)# line 83:
mydomain = inspiracode.net # (your domain name)# line 99:
myorigin = $mydomain
# line 113:
inet_interfaces = all
# line 118:
inet_protocols = ipv4
# line 165:
mydestination = $myhostname, localhost.$mydomain, localhost, $mydomain
# line 264:
mynetworks = 127.0.0.0/8
# line 419:
home_mailbox = Maildir/
# line 574:
smtpd_banner = $myhostname ESMTP $mail_name ($mail_version)
Note: using the vi editor, to show line number type:
:set nu
To go to a given line number type:
:[line number]
For example when going to line 100:
:100
At the end of the file add the following lines:
# limit an email size 10M
message_size_limit = 10485760# limit mailbox 1G
mailbox_size_limit = 1073741824#for SMTP-Auth settings
smtpd_sasl_type = dovecot
smtpd_sasl_path = private/auth
smtpd_sasl_auth_enable = yes
smtpd_sasl_security_options = noanonymous
smtpd_sasl_local_domain = $myhostname
smtpd_client_restrictions = permit_mynetworks,reject_unknown_client,permit
smtpd_recipient_restrictions = permit_mynetworks,permit_auth_destination,permit_sasl_authenticated,reject
# SSL/TLS
smtpd_use_tls = yes
smtpd_tls_cert_file = /certs/public.pem
smtpd_tls_key_file = /certs/private.pem
smtpd_tls_session_cache_database = btree:/etc/postfix/smtpd_scache
# use smtp2go as relay
# tryed gmail first, but changes FROM header to gmail address.
relayhost = [smtpcorp.com]:2525
smtp_sasl_auth_enable = yes
smtp_sasl_password_maps = static:user@smtpcorp.com:secret
smtp_sasl_security_options = noanonymous
smtp_tls_security_level = may
header_size_limit = 4096000
relay_destination_concurrency_limit = 20
Note: using the vi editor, to go to the last line type [G].
Also note the configuration for relayhost: As GoDaddy is blocking the outbound for email ports, we would be unable to send mail using our server to the world. One of our options is to keep trying to configure the REVERSE DNS records and research for port allowance options.
Instead, we have selected a relayhost provider (smtp2go).
You can use even your gmail, hotmail or any other private mail server account to relay your email, basically you will use that account to delegate the email sending functionality, postfix will be in charge of changing the headers for you, so the FROM field in your email looks like going from your account at this server (myaccount@inspiracode.net for me).
The problem that we faced with this approach was that when trying to use a gmail account, the resulting email remails with the gmail account in the FROM field, so when reaching it's destination, instead of showing myaccount@mydomain.com it was showing myaccount@gmail.com.
The problem was fixed opening a smtp2go account: for an affordable price, you can get a decent amount of email traffic. You actually have 20 daily free emails!
The trick is to configure the smtp_sasl options to connect to your account; in my case I'm using static option to specify username and password in the same configuration file.
If you have any troubles configuring this sasl options (or postfix not accepting them), try installing the following sasl tools:
$ sudo yum install cyrus-sasl cyrus-sasl-lib cyrus-sasl-plain
Now we Install Dovecot:
$ sudo yum install dovecot
Dovecot configuration
listening protocols and IP addresses ; . To configure dovecot execute:
$sudo vi /etc/dovecot/dovecot.conf
# line 24
protocols = imap pop3 lmtp# line 30
listen = * # ipv4 only (as goDaddy VPS does not give you an IPv6 address)
authentication methods
$sudo vi /etc/dovecot/conf.d/10-auth.conf
# line 100
auth_mechanisms = plain login
mail location
$sudo vi /etc/dovecot/conf.d/10-mail.conf
# line 30
mail_location = maildir:~/Maildir
postfix smtp-authentication
$sudo vi /etc/dovecot/conf.d/10-master.conf
# line 96-100
unix_listener /var/spool/postfix/private/auth {
mode = 0666
user = postfix
group = postfix
}
email traffic encryption
$sudo vi /etc/dovecot/conf.d/10-ssl.conf
# line 8
ssl = yes#line 14, 15
ssl_cert = </certs/public.pem
ssl_key = </certs/private.pem
Note the location of the certificates, that's the location that we stated in the last post.
Finally we will install a log tool:
$sudo yum install rsyslog
With those tools installed now we enable our email server to start on reboot:
$sudo systemctl enable rsyslog
$sudo systemctl enable postfix
$sudo systemctl enable dovecot
Finally we start the server components:
$sudo systemctl start rsyslog
$sudo systemctl start postfix
$sudo systemctl start dovecot
Your server should start smoothly, if it does not, please feel free to post your issue.
You can see what's up with your email server by looking at it's log at:
$sudo tail -f /var/log/maillog
or
$sudo less /var/log/maillog
[F] - To tail the file
[G] - To go to the last line
In the next post we will setup HTTPS and email client.
Regards.
--D